CyberSecurity
How We Keep You Secure
OUR PROCESS

Security Strategy Consulting
Enhance teamwork, communication, project alignment effectively, fostering collaboration.

Cloud Security Consulting
Expert guidance to secure your cloud infrastructure and ensure data protection.

Vulnerability Managment
Automate building, testing, releasing software reliably, speeding up development.

24/7 monitoring
Deploying the final product.
CYBERSECURITY
Don’t move, We’ll Handle Everything
Expert Support
Staff that engage daily with customer data and have skills and expertise in threat monitoring, detection and hunting, threat intelligence (TI) and incident response. See where expertise meets dedication.
Turnkey Delivery
Our human-led, turnkey approach utilizes a predefined tech stack covering endpoints, networks, logs, and the cloud. Expert threat hunters and incident managers analyze telemetry within the platform, delivering tangible outcomes for businesses.
Out-of-the-Box
24/7 remotely delivered detection and response functions. Continuously monitor and respond to threats round the clock.
Collective Defense
Quickly respond, investigate, and contain threats with efficient triage. Investigate and manage responses to threats without limitations on volume or time.
Proactive Security
Security assessment and validation to analyze efficacy
Provider-Operated
Provider-operated technology stack for real-time threat detection, investigation and active mitigating response.
END-TO-END
How our Solutions Work
How We Provide Ultimate Protection.
Seamless Integration with Your Existing Infrastructure
Cyber InsureX MSSP solutions deliver seamless, 24/7 protection against cyber threats.
Our team handles continuous monitoring, threat detection, and incident response, giving you top-tier security without the cost of an in-house team.
Stay protected, save money, and focus on your core business with confidence.
Streamlining Secure IT Operations for Peak Efficiency
Cyber Sainik’s Secure IT Services provide a strong, reliable shield for your digital infrastructure.
With proactive monitoring, advanced threat detection, and rapid response, we keep your systems protected from evolving cyber threats.
Our expert team and cutting-edge tools help minimize downtime and safeguard sensitive data — ensuring your operations stay secure and resilient.
Complete Risk Mitigation

Cyber InsureX Complete Risk Mitigation services help you spot and stop risks before they become threats.
We provide detailed risk assessments, strategic planning, and tailored security measures to keep your business protected.
By focusing on early detection and prevention, we strengthen your resilience and keep operations running smoothly.
Comprehensive Security Management
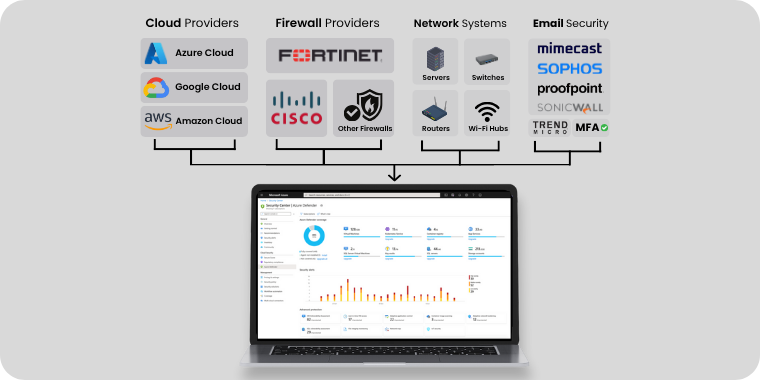
Cyber InsureX expertly manages and secures top tools like Microsoft, Cisco, Sentinel, Palo Alto, and CrowdStrike.
We handle configuration, monitoring, and maintenance to keep your security systems running at their best.
With our team managing your tools, you get stronger protection, smoother operations, and peace of mind that your digital assets are safe and resilient.
You ask, we answer
We believe you should feel confident about how we protect your business. Here are some common questions to help you understand how our security services keep you safe, resilient, and prepared for whatever comes next.
We provide around-the-clock monitoring and management to detect and stop threats before they cause damage. By strengthening your security posture, we also help lower your cyber insurance premiums because insurers see you as less risky to cover.
It’s best to protect your business before an attack happens. Building strong defenses now can prevent major losses, downtime, and costly recovery later.
Pricing depends on your business size, the sensitivity of your data, and your security needs. We create tailored solutions that fit your budget and give you the best possible protection.
We don’t expect you to be caught off guard. Our security stack combines modern threat intelligence, cybersecurity best practices, and immutable cloud backups that keep your data protected and recoverable. With these layers in place, the risk of a breach is already minimal — and for added peace of mind, your cyber insurance provides full coverage if the unexpected ever happens.
